
Cyber Readiness Playbook, Guides & Tips, Focus on Cybersecurity Issues, SMBs and Cyber
The Cyber Readiness Playbook
At the Cyber Readiness Institute, we believe being cyber ready starts with a few practical...

At the Cyber Readiness Institute, we believe being cyber ready starts with a few practical...

The Cyber Readiness Playbook Guide is a concise companion to...

The Cyber Readiness Institute (CRI)’s...

The Cyber Readiness Institute (CRI)’s 2024 Global Multifactor...

The “Playbook Verification Checklist” is designed to assist coaches in assessing...

The Cyber Readiness Institute (CRI) requires all of an organization’s employees and contractors...
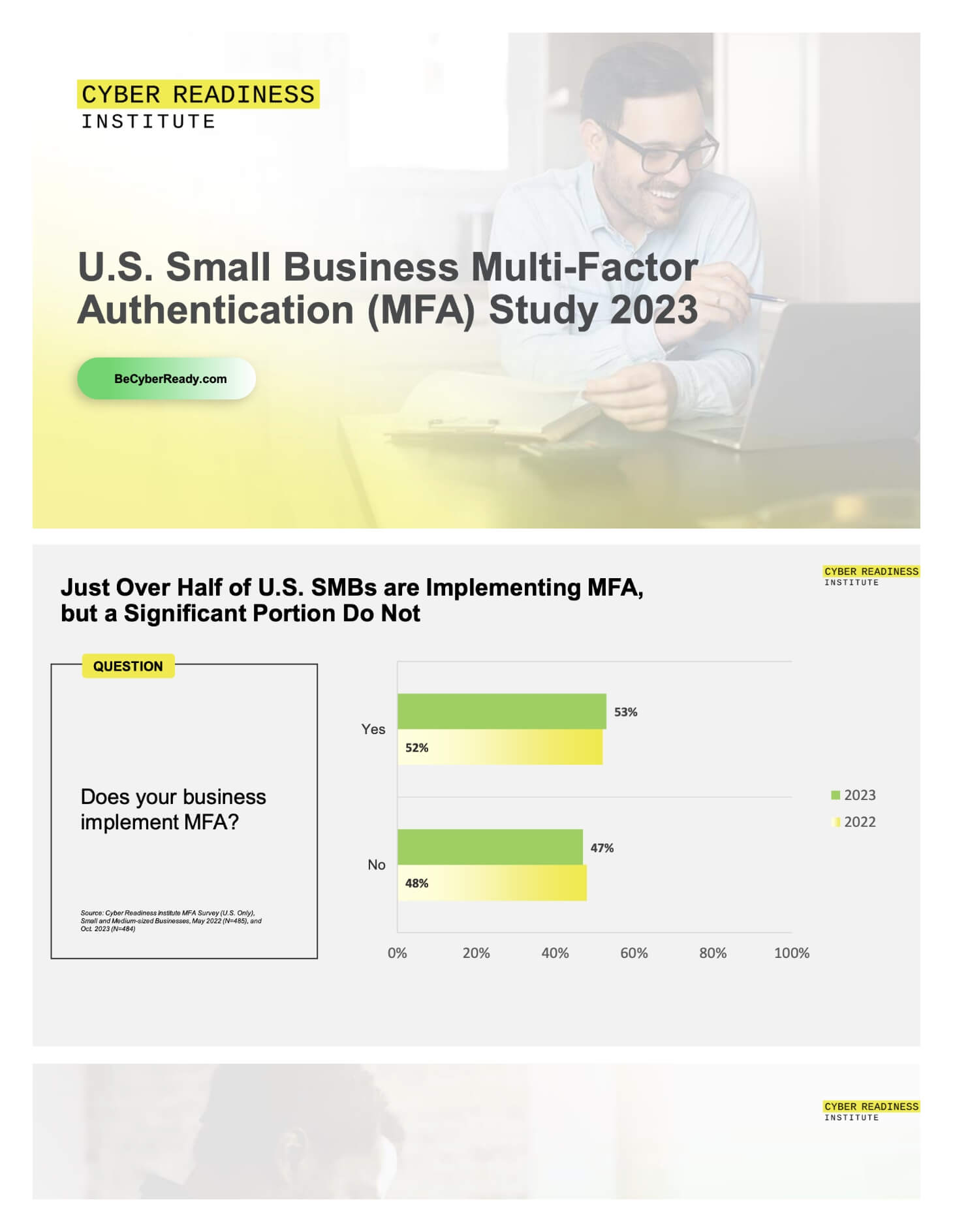
In Oct 2023, the Cyber Readiness Institute conducted its second...
Our nation’s educators and students are in uncharted territory as remote learning becomes...
Use this worksheet to help you keep track of the software updates required to keep your organization...
If you are building a culture of cyber readiness at your organization this resource will help...